Sponsored by NICE Actimize
Sponsored by NICE Actimize
Accurately Understand Your Customer Risk with CDD
Sponsored by NICE Actimize
In Pursuit of KYC Modernization: Translating Customer Data Into Intelligence
Sponsored by CyberArk
Mitigating Linux and Windows Server Endpoint Privilege Security Risks
Sponsored by Palo Alto Networks
Defending Against Modern Web-Based Threats
Sponsored by Palo Alto Networks
The DevSecGuide to Kubernetes
Sponsored by Palo Alto Networks
The DevSecGuide to IaC Security
Sponsored by Palo Alto Networks
The Power of Next-Generation SD-WAN with App-Defined Fabric
Sponsored by Palo Alto Networks
Why You Need Next-Gen SD-WAN
Sponsored by Palo Alto Networks
Top 10 Considerations for Your Next-Gen SD-WAN
Sponsored by Palo Alto Networks
Multicloud Mastery Requires a Modern Approach to Cloud Security
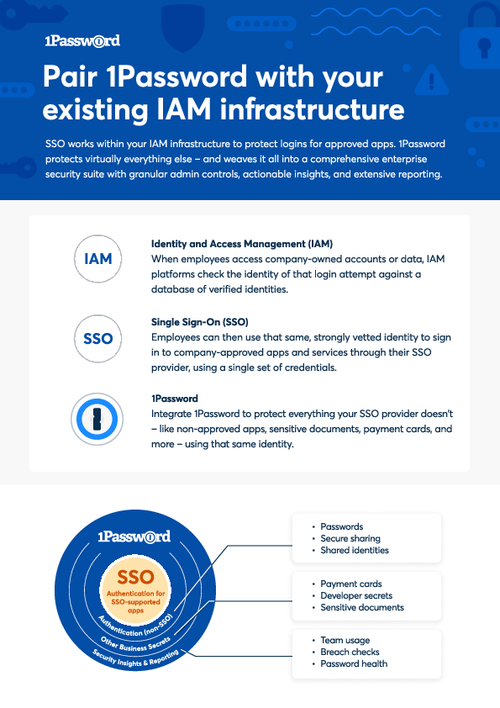
Sponsored by 1Password
How to Pair Password Security with IAM
Sponsored by 1Password
It's Time to Get Serious About Enterprise Password Management
Sponsored by 1Password
7 Steps to Successful Password Security
Sponsored by 1Password