Target Analysis: Could Have, Should Have
Senate Report Only Scratches the Surface on Mitigating RiskAn analysis of the Target breach prepared for a Senate committee offers about a dozen "could haves" - steps the retailer might have taken to prevent the breach that compromised 40 million credit and debit card details, as well as personal information of 70 million customers.
See Also: When Every Identity is at Risk, Where Do You Begin?
"A 'Kill Chain' Analysis of the 2013 Target Data Breach" - the report for the Senate Committee on Commerce, Science and Transportation - does a fine job relating IT security and risk failures by Target and one of its contractors, whose stolen credentials apparently allowed the hackers to access the retailer's point-of-sale system, where customer financial information was pilfered (see Senate Report Analyzes Target Breach).
The report is a political document, and might help its patron - Sen. Jay Rockefeller, the West Virginia Democrat who chairs the committee - advance a bill he introduced that's designed to get retailers and other businesses to tighten their information security practices (see Target CFO Grilled in Senate Hearing). But the analysis is not a technical document, one that provides more detailed advice to enterprises to prevent the mishaps that led to the Target breach.
One of the most noted "could haves" deals with the lack of use of two-factor authentication. The bad guys reportedly gained access to Target's system through stolen credentials from Fazio Mechanical Services, a Sharpsburg, Pa.-based contractor (see Target Vendor Acknowledges Breach).
"The malware on Fazio's systems may have recorded passwords and provided the attackers with their key to Target's Ariba external billing system," the Senate report says. "... Target could have potentially disrupted the attack by requiring two-factor authentication for its vendor. ... According to a former Target vendor manager, Target rarely required two-factor authentication from its low-level contractors."
Fazio had access to Target's network for purposes of electronic billing, contract submission and project management. Some experts believe the hackers tunneled from the periphery systems available to Fazio to the POS system.
The Senate analysis champions a framework known as an "intrusion kill chain," in which network defenders should continuously monitor their systems for evidence that attackers are trying to gain access to their systems. A paper by the intrusion kill chain framework developer, Lockheed Martin, says attackers must proceed through multiple steps to execute an attack. While the attacker must complete all of these steps to execute a successful attack, the defender only has to stop the attacker from completing any one of these steps to thwart the attack.
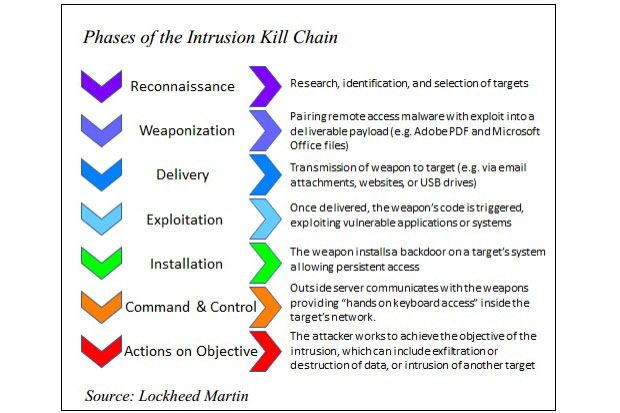
The intrusion kill chain suggests multifactor authentication would have prevented the breach, according to the Senate study. It might have. Fundamentally, though, Target and other enterprises must architect systems to make it impossible for contractors, employees or anyone without a need to know to reach the parts of their systems containing sensitive customer and other vital information.











